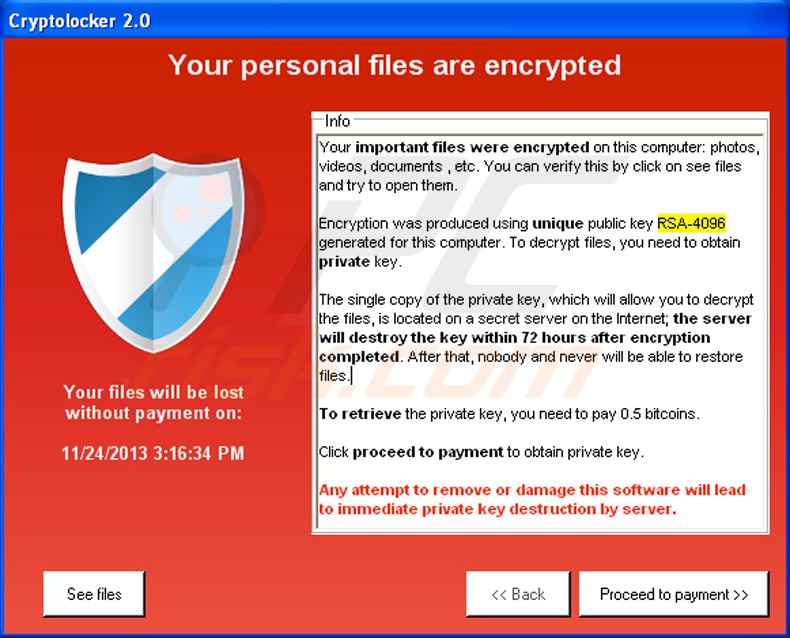
Every day someone finds something. This day was no exception. The more creative the attack the more interesting the day. If you call that number they try to get you to give them $199.00 to unlock your computer.
You can send me some money if you like but, here is the fix for this…
CTL ALT DEL , task manager, kill the process, aka browser and then do not restore the page when you reload the browser.
I am not affiliated with CCleaner but I sell a heck of a lot of it for them. Install it and let it clean your browser after every use. $25 a year and damn well worth it!
As one might use an explicative to emphasize a point, I often use a somewhat tawdry analogy for this purpose. Surfing the web with inadequate anti-virus software is like “hooking up with a stranger” without using protection. Not only is it idiotic, but dangerous!
Having been in Data Processing, or the IT business since before Steve Jobs or Bill Gates was a household name, I know a thing or two. The scars on my back are from arrows taken in the trenches of digital mayhem. This bedlam was caused by such things as bosses wanting to be on the bleeding edge, to software not ready for prime time, been there done that.
Free antivirus software is not worth what you pay for it!
The best security software is going to have a price or cost to it. Why? It takes many engineers, coders, and much research to create and maintain a massive program like anti-virus software. Who is going to do that for free? More importantly, why?
While someone might write an app for free, to get their name out there; anti-virus software takes a village.
Much like hiring someone to sell your home, you don’t hire someone who does it part-time or as a hobby. If you want to get something done, give it to a busy person. If you want to sell your home, hire someone who’s lively hood depends upon them being successful. You want a secure computer, hire or purchase the product with the most to lose if it fails.
There is much more to the process of considering which product to purchase but, free is not a reason. I would argue that free is a cause to eliminate that choice.
The reality is that the internet has become the wild west. The bullet that finds you can come from almost anywhere. Every company that uses computers should have a security officer. His or her job should be to focus their attention on threats out there and the best way to keep them from affecting that company.
I find it surprising that politicians are screaming about Russian hacking of our computers. What the hell do you expect? You just assume that someone with a certification gives a damn!?
What worked in 1982 does not work now. Having a “PC Wizard, or your grandchildren” working for you is tantamount to a trapeze act, blindfolded and working without a net. Insurance companies and credit card companies are now aware of this and demanding your strategies to be secure in the world of cyber threats. They should audit you, and they should hire folks like me who know what to look for.
White Hat hacking allows us an inside look at what one might expect. We learn many ways to infiltrate a company. The same applies to the TSA in homeland security. While I would probably choose a job to be that guy that test the security systems of the homeland, airports and such, it is much easier to check companies.
The first thing I must do is understand you. More importantly, know that entity many of us in the biz call “users.”
Too many infiltrations are accomplished with something called click bait. “Ten pictures that should never have been made public…” With half a picture of some scantily clad woman visible, how many will click?
Human nature dictates men will want to see what the camera saw. “Boom, you’re infected.”
Good antivirus software will stop any activity created by software manipulation but, the caveat or keyword there is “good.” What if you bought the bargain basement software or just used the free stuff?
For the coders to write the fix, someone must fall prey to it, report it, and then they must institute a fix. That is why Software of this type is never static. Updates are consistent and often. New threats are released hourly. To run a company dedicated to this is no small task.
Maybe you own a plant which produces widgets. Your widgets are better than others, and your competition wants the skinny. You hired someone like me for your IT manager or CIO so they cannot get in through your firewalls. Your safe, or so you think. Industrial espionage is rife in the competitive world of gadgets and widgets. If I want in bad enough, I will contract one of my guys to write a program that will hide on a computer until certain key phrases are typed, and then it will activate.
“Wait, you said my firewall is secure, Fort Knox secure!”
“Why yes I did, so I am going to place this little program on a thumb drive and…I am going to put some naughty pictures on it with some commercial looking writing on the outside of the device to make the person who picks it up from the parking lot where I dropped it, think that they have something juicy.”
Possibly just tossing a thumb drive out the window of my car near the parking lot with a few files on it, and the Trojan would be enough to get me into your network. I will purchase some chrome colored or fancy looking thumb drive to be sure that it is spotted. I will know when the landscape folks work, so I make sure and plant it after they have done their thing so that one of your employees will find it.
Maybe I send one of my spies out to places that your guys eat and leave the drive on the table by the ashtray or the salt and pepper shaker at the table they eat every week on a given day and time.
Possibly I get one of my people inside your company, hired by you. They install some remotely controlled program like Team Viewer on their PC and Viola; you are hacked.
Because your IT guy is so sure that his firewall is good enough, or your engineers are so demanding that he left the USB ports open for use by them, with lax policies he leaves your company vulnerable too.
How do we stop the threats?
One way we do this is with training. Every employee should sit through CE training on the essential use of the corporate computers. This is information that they can bring home and share. Education is by far the best tool one can have in their arsenal.
All of the policies are trumpeted for them to hear and before they leave they sign a document saying they will adhere to them. With it harder and harder to fire people these days, that too is one more tool in your belt. Good employees, you want to keep, those that prove lacking, they need to go.
I could easily make the argument that good computing practices are patriotic. I could certainly apply this to purchasing respectable anti-virus software and creating policies and procedures that protect your business but, the bottom line is, in the end, it will save the company money.
I was making this argument to a CEO of a good-sized company when he stopped me and said, but viruses help your bottom line too.
I argued that I would much rather use my time and talents to design safe environments for companies like his than put out fires. It is considerably less expensive to install a good fire retardant system then to try and rebuild. Yes, a metaphor for using robust best practice standards in computing vs. reacting to noise.
Noise is the result of a problem created by an event that was unplanned or caused by employee error.
A good security person is somewhat paranoid and is always asking, what if? I do this in disaster recovery scenarios balancing those “what if’s” against statistics and a risks assessment.
With proper education, we can mitigate the employee errors. Using proper procedures and policies, we can diminish the unplanned events, i.e. viruses or other malicious code.
When I run into companies that think free antivirus software is adequate, it makes me a little crazy. If they are a public company, trust me, I will not purchase their stock. Flirting with disaster out of sheer frugality or ignorance is idiotic.
If you keep your guys around because you like them, think again. I may love some folks, but I would not hire them for certain positions if I could find someone better. I don’t have to like you, for you to work for me. If you are the best person for the job, you get the job. P&L trumps feelings! Feelings can be costly and can be a liability. Logic in business is your ally. Logic must always be forefront when making business decisions.
I have walked away from companies who have their kids working for them. By hiring the children, you open yourself up to losses that could be untold. One company had their children not doing the paperwork necessary to complete the task, thus losing money in that department. Hiring me to do an analysis, it did not take long to find the problem. I fired her children after trying to work with them. I kid you not one of them actually cried in my office after telling him time after time he must do all of the job. A grown man crying! There is no crying in IT. Either perform the work or get the hell out! Either do all of the job or learn to ask, “Do you want fries with that?” Is that too tough? I felt for the kid but, feelings do not dictate policy.
Do your kids a favor and don’t hire them. The real world does not work that way so why in the world handicap them, and make them believe that it does?
Over the years there are best practices that have been created by time trusted procedures and policies.
Some are things like:
- Hardware Asset management.
- Software Asset Management
- Security both physical and digital
I could write a book on the subject, but I will spare you the details.
Today, now more than ever we must harden our networks. We must have sound policies and procedures in place, and they must be adhered to. Documentation is essential, and it must be updated.
I don’t relish firing people but, sometimes their people are the problem, and the CEO is so far removed from the process they just don’t know it. If training can fix it, I am all for it. Attitude too plays a crucial role in the process, and I will not tolerate a crappy attitude. Life is too short, and the subject matter is too important.
I love the HR folks because often they are the gatekeepers, saving the CEO from disaster. Good HR folks are worth their weight in silver. Gold, maybe not, so let’s stick with silver. Worthy people are not that hard to find as many would have you believe. Upright people are around, but they may not have everything that you are looking for immediately.
Instant gratification is an expensive luxury and can be elusive at best. Where employees are concerned, I want to start with a “good foundation.”
We place certifications above character, and that is part of our modern day conundrum.
I hired a grocery store manager and trained him for a job in IT. He had little experience in the job I hired him for, so why did I hire him?
He had the right attitude and wanted to learn.
I had the time to train him.
The money used for training him was penny’s compared to hiring exactly what I was looking for.
He did not have the bad habits that come with so many “experts” with the certifications, and their egos.
He ran a grocery store and let me tell you; he was not afraid of work!
Back in the day, we had interns or apprentices. Folks, we need to look carefully at that once again. I have hired many over the years that had the right attitude and the skill set to learn. American people are out there struggling, and we won’t give them a chance. Why? Instant gratification. We need someone who can step into the job right now, and we run with minimum employees because of what? Because it is so expensive to have employees.
That is one of the things we need to push back on Congress and health care to fix, but the reality is, internships and apprentices I think are essential to finding and creating good employees.
Every job fair that I go to has thousands of workers looking for work. If you can’t find them, you are not looking! I spot good employees daily. There are times I would love to go work for a recruiter just because I can spot talent!
Are they the exact racehorse ready for the Derby today? Maybe not, but can they be trained? There are virtual diamonds in the rough everywhere, looking for a chance! We are begging to bring in more H1B folks instead of taking care of our own. That is not very damned patriotic if you ask me!
Our schools are a disaster in my opinion. In speaking with college graduates today, I am frequently amazed at just how ignorant and totally out of touch with reality that they are. Someone somewhere screwed them to the tune of tens of thousands of dollars for an education that is worthless. When they think voting for a socialist is a good idea, they were screwed by their college and should demand their money back!
Today we have kids tens of thousands of dollars in debt, and they cannot find a job. I know of several college grades making much less than $15 an hour. Our educational system needs an overhaul.
As quickly as a company can get a process documented and packaged, they send it overseas via a VPN over the internet, sending jobs out of the country.
Trades are being overlooked for white collar jobs which are going the same way. IT jobs are vanishing in the states. Virtual IT shops are set up in some foreign country, hiring an English speaking American to act as a liaison between them and their Indian or other counterparts. With an American point of contact, it is then up to the American to manage the folks in another country who speak little English, making little money, to be the IT shop for these American companies. This same person puts an American face on their business while working with their client managing the “noise.”
“Do you see any security risk there?”
You have no clue where your intellectual property is going or who is seeing it. Maybe you have a contract but so what. Much like HIPAA was created to protect your health information, do you honestly feel as if your information is secure? If you do, you are fooling yourself. Read the documents you sign when you visit the doctor. You sign things saying that your information is protected and then you sign a document which pretty much gives them a pass to do whatever they want to do with your information. Smoke and mirrors.
Doctors and hospitals are hacked and the information is stolen all too often. Why? How? Piss poor planning on someone’s part. Using some cheap method to get things done perhaps?
Your contract with your Virtual IT company is as worthless as the paper it was printed on. Yes, that deal might make you feel better but, know if you are a developer, someone in some other country has your work and if they can use it, they will.
I want to touch on Software Asset Management as it is germane to this subject. All of the subjects are salient, but that one, in particular, is in the case of security.
There are tools which you can use to inventory every program on every PC. Why? Why would you want to do this?
Licensing of software is an issue, but more importantly, you should want to know what is on those PCs. The first time I did this for a company I was struck with the reality of the sheer number of programs designed for remote control of a PC, that was active.
In this world we live in, corporations can ill afford to have the wild west inside their computer networks. Besides the games and other foolishness that was identified, the risk to the infrastructure was phenomenal. The company is liable for every program on their PC’s, no matter who put it there. If they are audited for their licenses, and someone like myself does an audit and finds them, they must then produce that license. Can you? Can you put your hands on all of your licenses?
Ignorance is no excuse!
Having been part of the evolution of the business process, dating back to the secretary and the typewriter to current day, I have seen the learning curve first hand. Fighting the first virus on a network before there was anti-virus software; asking “what if” became second nature.
Back when Gregg shorthand was used, a business letter cost an average of $100.00 back then. Now we type out e-mails with the ease of few keystrokes and dictation is a thing of history. Technology has improved the business process, but the bad guys have found a way to make it interesting.
The very tools we use to make our lives easier are under constant threat by evil forces that look for ways to extort money or steal your property either through the exploitation of your network, or your employees themselves.
We use the cloud as if it were a hard drive in some vault in our closet. We send information to the cloud without a clue where the cloud is and who has access to it. Why we don’t encrypt that data before it leaves our computers is beyond me. If I were a villain, I would be looking for ways to infiltrate the “cloud.”
“What if?”
The opinions expressed are my own as well as the intellectual value of the information put forth for your consumption.
© All Rights Reserved 2017






















































You must be logged in to post a comment.