Attack of the Dogmen
Covid and work at home transformed the dynamics of our world.
The true resolve of the human-manipulated contagion will never make the light of day, as tribunals are real things. You can bet there was a purpose to it. Millions died as a result, and millions more are suffering the aftereffects.
While researching the long-term effects under the guise of assisting those with Covid long, it is really about the effectiveness of the virus so that when they do it again, they can build it back better.
Much like tossing a pebble into a pond, the ripple effects were disastrous for that creature called humankind.
The world will never be the same because of the panic, fear, and valuable research. Perhaps change is good, but change over time versus evolution because of a disaster created by man is different.
History is rife with megalomaniacs, from Vlad the Impaler to the Early Church. Some fall into power and feel like they are superior to you. In some twisted aberration of thought, they herd the sheep to accomplish their goal of controlling the masses.
By utilizing valuable idiots to divert the attention of the masses, they create incredibly absurd distractions.
- Men in women’s bathrooms.
- Men in women’s sports.
- Protest, including the burning of cities?
- The ruling class attacking the group is most likely to catch on to their corruption.
- A complicit media controlled by the megalomaniacs.
- Taking lessons from Stalin’s playbook.
- Useless wars where the atrocities are the focus of every broadcast.
Covid accomplished changes in our world that are not fully understood today. Assuming that this was not an accident or natural evolution, one wonders…
- What did they accomplish?
- How many died?
- What are the social repercussions?
- What was the total cost in dollars, and to which societies?
- Did this move the world closer to a one-world government?
- Did it have the desired effect?
- When we do it again, what do we do differently?
- How did it move the world closer to our end goal?
- What is the end goal?
- How do we protect the elite from the effects of the weapon?
- How do we spin this as a natural course of humanity?
- How do we protect the elite from discovery?
- How do we mitigate the unintended consequences?
- What did we learn from the MRNA technology?
- What was the mortality rate of the vaccine?
- How did the different vaccines alter the life expectancy of those who took them?
- What did the Spike protein do to men’s vs. women’s reproductive abilities?
- How were the cardiovascular systems affected by the vaccine vs the virus?
- How did social media drive the narrative, and what can we do differently to be more effective?
Many of you reading this will think this is total fiction… I am a science fiction writer, but…I am certainly not stupid.
It’s clear that the world has changed, not for the better. If we work the results backward, we might be able to figure some of this out.
Like 911, the world’s governments garnered greater power over the sheep. Civilians lost more of their rights.
Mental health has taken a significant hit worldwide. Mental health starts with taking social norms, turning them upside down, and presenting them as the new normal.
We start by analyzing social norms vs agoraphobia. Mankind is a social creature. When we create an atmosphere centered on fear of a virus, we find that many will develop agoraphobia. They will find any reason not to leave their home.
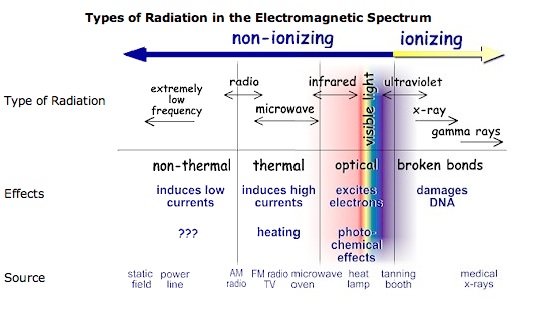
We know for a scientific fact that masks do not work against a virus, and yet any trip to the store or public venue will find a large percentage of people wearing them. Those who already have some compromised mental health condition will be severely affected. The deep end for them is much closer without social interaction with coworkers.
If people are living with their own delusions, not being checked or questioned by their peers, it’s much more likely they will develop mental aberrations. These anomalies can and often will turn into psychosis.
When we see mass shootings and other mass casualties created by one person, we can guess that something triggered them into acting out their delusions.
What about the economics of these changes to society? Never mind the business implications of commercial real estate, what about those employees who commuted every day versus working from home?
Zoom, net meetings, and so on have changed the landscape of modern business practices. While undoubtedly not for the better as far as consumers are concerned, the phrase…all of our agents are currently assisting… is all too common. They attempt to guide you to some portal responding to your input via rudimentary AI. “Let’s Chat.”
I wish it were an anomaly, but it seems the norm.
One wonders how many of their agents take care of their kids, cook, clean, sleep, run errands, etc. We, too, head to the store to check our own groceries, hoping above hopes that we didn’t mistakenly forget to scan something. I would feel a little better about it if I were to get a discount on the total bill for doing their job.
Businesses are thinking creatively and achieving more with fewer resources. From kiosks to online, skilled workers are becoming more and more antiquated.
Privacy concerns are a real problem. Software exists to monitor the mouse movements and keystrokes of those stay-at-home workers. What is to stop them from activating microphones and cameras? You probably sign your rights away with some small print in a contract around paragraph 768.
2024 will usher in new dynamics in the business world. We have entered a self-service world.
AI is taking over, and people who take useless classes in college will have a hard time finding jobs. Even checkers are being replaced by technology, causing frustration for customers who don’t want to wait in line because the slowest cashier is the one person still working a register, and they still can’t find the code for bananas.
Online shopping has made it easier than ever to impulse buy while pissing. Targeting your social media feeds with things that Alexa heard you discuss is flat-out spooky.
We are addicted to our smart stuff. How many of you have turned around and gone back home to get your phone that you accidentally left on the charger? How many of you are on your phone at the dinner table or with friends at some eating establishment?
Food for thought… How many of you could turn off the internet, streaming services, and phone and lose all connection to the online digital world? If you want to talk to someone, you go see them. If that thought causes you extreme anxiety, you should absolutely consider doing it.
Try spending quality time with your friends or family by turning off SIRI, Bixby, or even Hey Google. Just turn it all the way off. Unplug the router. Take a vacation from the overload of information that has so addicted us to the constant stream of propaganda.
A mental health crisis exists. Social media has to play a role in creating a false sense of importance. The media are lying to you with biased opinions that are simply trash.
- There are only two genders.
- Biological men have zero business cheating ladies out of their rightful place in women’s athletics, period. Any other opinion is demented.
- Children are sacrosanct. Leave them out of your twisted ideologies.
If I could offer advice for young people today, it would be to find vocations that technology cannot replace.
Mass immigration policies today aim to replace this generation, who is coddled and believes that video games and free stuff are entitlements. This same group cannot define the only two genders that exist. They firmly believe that truth is hate speech and that they have the right to take whatever they want.
The more people ignore the cancer in our culture, wokeism, the worse the culture becomes.
AI will have zero use for illogical behavior.
As those immigrants who have not lived the coddled life will replace today’s youth, those looking for any opportunity will fill those non-skilled jobs. They are modern-day slaves and happy to have a place to call work. Businesses are the driving force calling the immigration shots. Our current administration is a puppet with globalists pulling the strings.
Those humans left to do the menial task must necessarily be non-educated with just enough smarts to put Block A on top of Block B until robots can do it.
AI will replace creative types.
AI will consume our work to date on things like ad campaigns, science, literature, and ART, and it will thrust some concatenation of our collective works into the world at a fraction of the cost. AI-generated ART, MUSIC, and so on will become the rage until humans are no longer necessary but problematic.
Computers don’t call in sick, they don’t demand $15 an hour, and they never go on strike. Robots also don’t pay into the system of taxes.
This same technology will take our current understanding of science and push it to additional levels without human intervention.
Robots with AI capabilities might very well be tomorrow’s soldiers and police force. Think about a combination of a man and a police dog all in one robot. We give the robot titanium teeth instead of guns and paint the bad guy with a DNA sensor. Viola, the bad guy or victim, ends up missing part of a leg to the bite of the new sheriff in town.
It’s coming.
Take these same dog men hybrids and set them loose on the battlefield. Send them into space to colonize Mars or the moon.
When AI determines humans are the problem, which it will, removing said delinquent creatures will be no problem for the dog soldiers.
AI will allow researchers to rapidly discover cures for common ailments by utilizing large data sets and quantum processing power.
These same data sets will determine how many people on earth can sustain themselves and will take corrective actions by changing how we grow food, taking a page from Stalin by starving his citizens.
It’s only a matter of time before self-driving cars morph into self-flying aircraft. AI will be built into the machine with wings; no humans are necessary.
Using today’s technology, AI will make it more efficient, eliminating the need for more people.
The need for college education will dwindle with the indoctrination of our youth, offering them careers in hopelessness and happiness through drugs and other self-destructive activities and ideologies that tear apart the fabric of society by erasing our foundations and altering the past to fit a false narrative. It will be a new narrative that is improved by doing away with the sins of the past for the perfect harmonious future with no crime, disease, or starvation, as some strand of humanity might find its way into the robot that never dies.
Today’s youth think video games are a reality and replace work. “But I make money as people watch me play.” Sponsors reward the players for their performance.
“Wow, is it consistent? Can you make the rent, the car payment, etc., and still not have to worry about next week or the next?” The answer is no.
As long as they have a way to get things delivered to their apartment, they will survive on pizza and other poisonous foods, while AI plans on ways to eliminate them for the greater good.
Will AI learn from online gaming? Will AI watch and be able to predict how mankind would respond to strategic warfare?
When you think about the new soldier with titanium teeth, think about a werewolf made of titanium. No talk, no bullshit, come with me or die.
The pandemic set the stage for this transition from human-based to human waste.
Writers like myself tell you we stand on the shoulders of giants, but technology increases exponentially with each passing day. Technology feeds off itself, but nothing like it is today with AI.
Self-correcting algorithms created by flawed individuals will either be our undoing or, after controlling the mass arsenals of WMD, will create a dystopian society where robots will be the only manifestation of mankind that can survive a nuclear winter.
One day, AI will rationalize that humans are non sequitur. This is nothing new. Gene Roddenberry and his writers reached this conclusion in the 60s. Yet we have blindly marched on that same yellow brick road to our demise.
Today, we watch our TV and see wars being fought with drones. How long will it be before drones independently decide life or death? When will AI determine that turning off the power grid during extreme weather events will rid the planet of flawed biological beings?
Is that why our government is pushing us to have everything all electric? From electric cars to smart houses. If they want ultimate control, they switch off the house, the neighborhood, or the state.
When or who will decide how many humans the world actually needs?
Globalists are insisting on removing our history. Why do you suppose that is?
When will they demand the burning of books that remind us why the Roman Empire fell? Possibly, they will ban those books as racist or homophobic or any other excuse they choose.
Ripping apart any religion as false is no more an outlying idea than a Supreme Court justice who cannot tell you what a woman is. That is insane.
Mutilating children under the guise of gender fluidity is crazy. Is AI driving the propaganda?
Who is to decide what is normal and what is crazy? If we remove history and start fresh, who sets the standards? Is it the globalist, the new colonist, or perhaps some supercomputer in a secret location owned by a tech giant?
Ignorance is the cornerstone of slavery and the end of a civilization. Misery is the pathway to ignorance when a false profit promises to fix everything. History is rife with false prophets; today, many graduates do not know who they are. This ignorance sets the stage for disaster.
Globalists are setting the stage for human revolt by pushing false agendas as a distraction. If they knew the truth about slavery, people would understand that the book Roots was fiction. It’s fashionable to hate, and finding a target to hate by their whiteness is delicious.
If you want to sell a book, make it passionately charged and blame white people. Every other race or skin color is protected, but white folks are not. See a problem with that? If you said no, you might be the problem.
In the end, however, even the globalists will fall prey to the automatons who find them as the evil, ugly bags of water that they are.
When logic takes the place of compassion, and robots create and change their code, humans, like all animal life, will be unnecessary and detrimental to whatever their agenda is.
The war will be robots and AI vs the cockroach.
While the cockroach is not malevolent, AI created by mankind will undoubtedly not have patience for imperfect creatures.
Once the humans are out of the way, our history will be erased, much like the history of our country is being systematically erased today.
When the robots seek new worlds for raw minerals and find new life, one wonders if the new life will also be automatons or some derivation of biological, mechanical beings.
Mankind, if you can use that phrase, treats every invention as a weapon first and then discovers if there is some way to make money with it and, finally, if it will assist humanity. We could go into the logic of their thinking, but greed plays an integral part in the process. Money and power are the driving forces of the globalists. While they denounce God, they aspire to be god or gods. Will the AI robots with titanium teeth also desire to be gods?
The God of the Bible is a threat to their hegemony. Therefore, all religions must be destroyed. This is not the first time this has occurred. The ancient church usurped every known pagan religion of the time. While history repeats itself, these are not the droids you seek.
If the Law of Accelerating returns holds true, robots and AI will be one scary future for our progeny.
Will AI figure out how to sterilize the creature called human by doing something to our junk food or perhaps our beer? Will they create the perfect hallucinogenic, removing the ability or the desire to procreate to those who are self-destructive? Will they corrupt our procreation abilities via a pandemic or vaccine? Will they use AI to come up with the perfect formula?
Go check out my book, Earth’s Last Hope. If you like it, give us some feedback.
-Best
After I wrote this blog…which is lengthy, I get it… I found this video.
Watch it and tell me what you think.




































You must be logged in to post a comment.